Interpreting events with log analytics
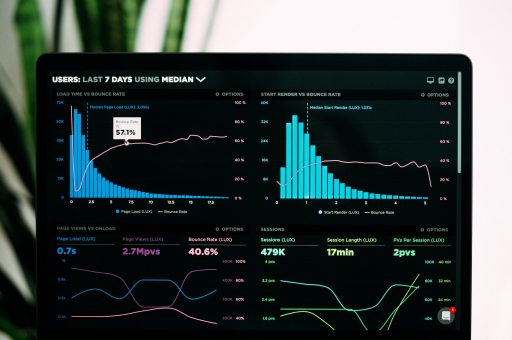

If the performance of your website suddenly slowed to a crawl, would you be able to pinpoint the cause of the problem?
If an intruder had penetrated your network and was sending data about your customers to a server in Russia, would you know it?
Are your security administrators so overwhelmed with alerts that they sometimes shut down the intrusion detection monitors so they can get more work done?
If any of these scenarios sounds familiar, then you should be using log analytics. That’s the discipline of capturing and interpreting events captured by computers, networks, operating systems and other technology elements that can be useful in helping you to understand better what’s going on inside your infrastructure.
These days log data is everywhere, but many organizations lack the time and skills to make the most of that information. Part of the problem is that the data comes in many different formats depending upon the devices, software components and versions each company uses. Part of it is the sheer volume of data, which can quickly overwhelm human analysts. As a result, many organizations fail to take advantage of the insights log analytics can provide.
« In the area of cybersecurity, log analytics can be a godsend. Machine learning algorithms can be trained to pore over historical alerts and identify those that correlate with actual security incidents. This greatly reduces false alerts and improves the productivity of security personnel. »
For example, log forensics and monitoring can be used to debug applications by comparing current and past performance. Statistical correlations can bring forward relevant factors that may be impacting performance, enabling faster resolution.
VMware just announced a major overhaul of NSX that pits the company directly against Cisco. Can you assess VMware’s performance in using NSX to expand out of its server virtualization niche?
There’s a report that VMware is about to align itself with Microsoft in a partnership similar to the one it formed with Amazon Web Services three years ago. What does this say about VMware’s confidence in its hybrid cloud role?
How well do you think VMware is doing at diversifying out of the server virtualization business with products like cloud management, digital workspace and desktop virtualization?
In November, Pat Gelsinger said “We’re out to change security in a fundamental way.” How well positioned do you think VMware is to do that?
You might also like


Risk and Compliance Governance
For a long time considered as a purely technical domain, we have been observing, for a few years now, a paradigm shift in cybersecurity management.


Identify and prioritize cybersecurity investments
In order to produce the information security action plan, the initiatives should be carried out over a period of time based on various factors that are well known in project portfolio management, such as the company's strategic orientations, the availability of resources, etc.

